Features and support of the mobile application
The main task of the application is to display the user’s tasks (eg security guard) that he has to perform on a given day and those that have already been done. Through it, you can generate and send a report, report an incident, and register the start and end of your change.
Thanks to the intuitive interface, the user has an easy overview of procedures, can quickly and intuitively report occurrence of individual events as well as can report an alarm.
The application is available in many language versions, including Polish, Spanish and English.
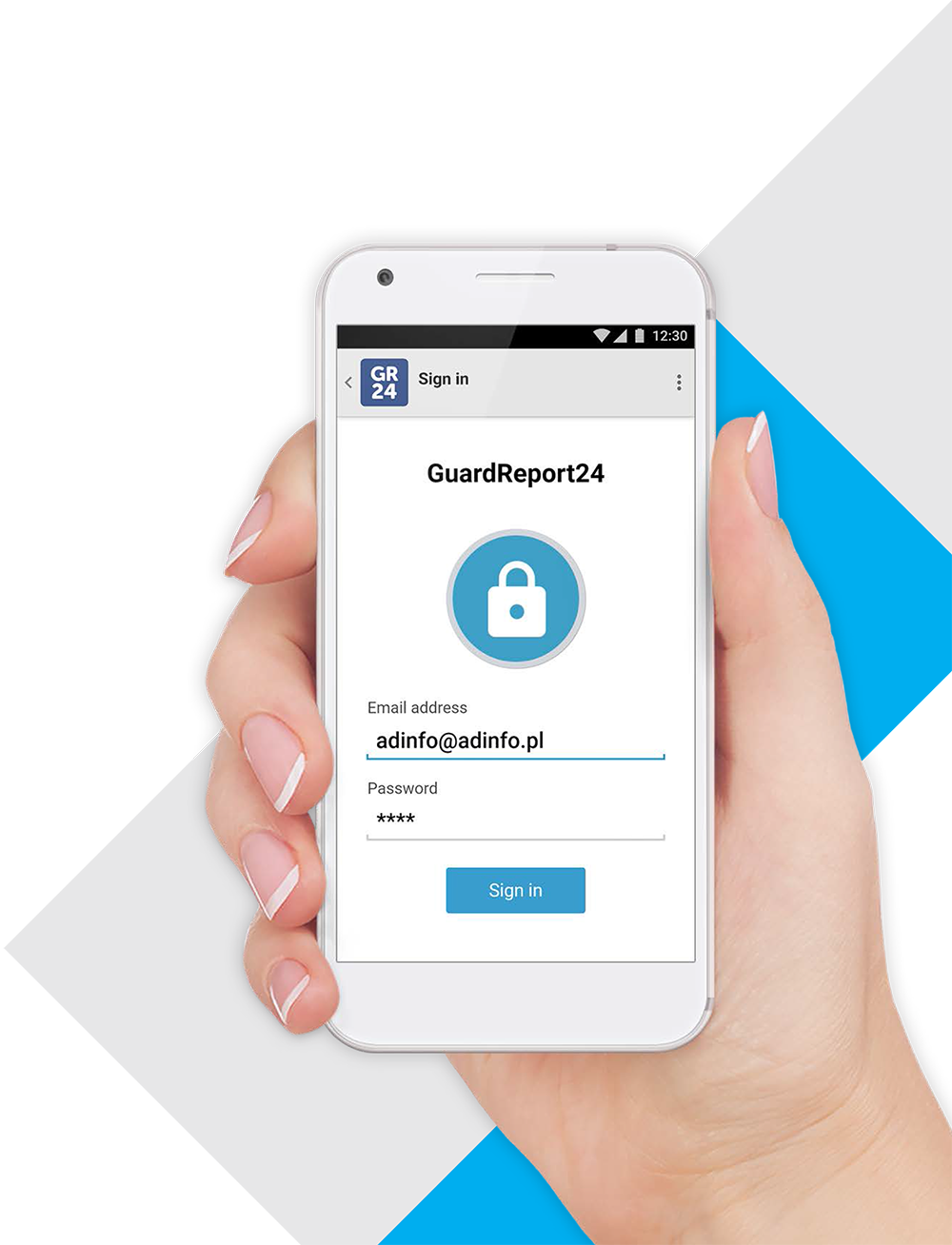
Logging in to the application
The user logs in to the mobile application or to the web application with the help of a unique login and password, which are broadcast in the WWW application (in it also the permissions for objects and activities available to the user are defined). Each login is logged (time information, login place etc. is saved) and if necessary, you can get this information easily and quickly.
All connections are encrypted to ensure maximum security. Additionally, it is possible to limit the number of incorrect logins, eg up to 3, which will protect the device against unauthorized access.
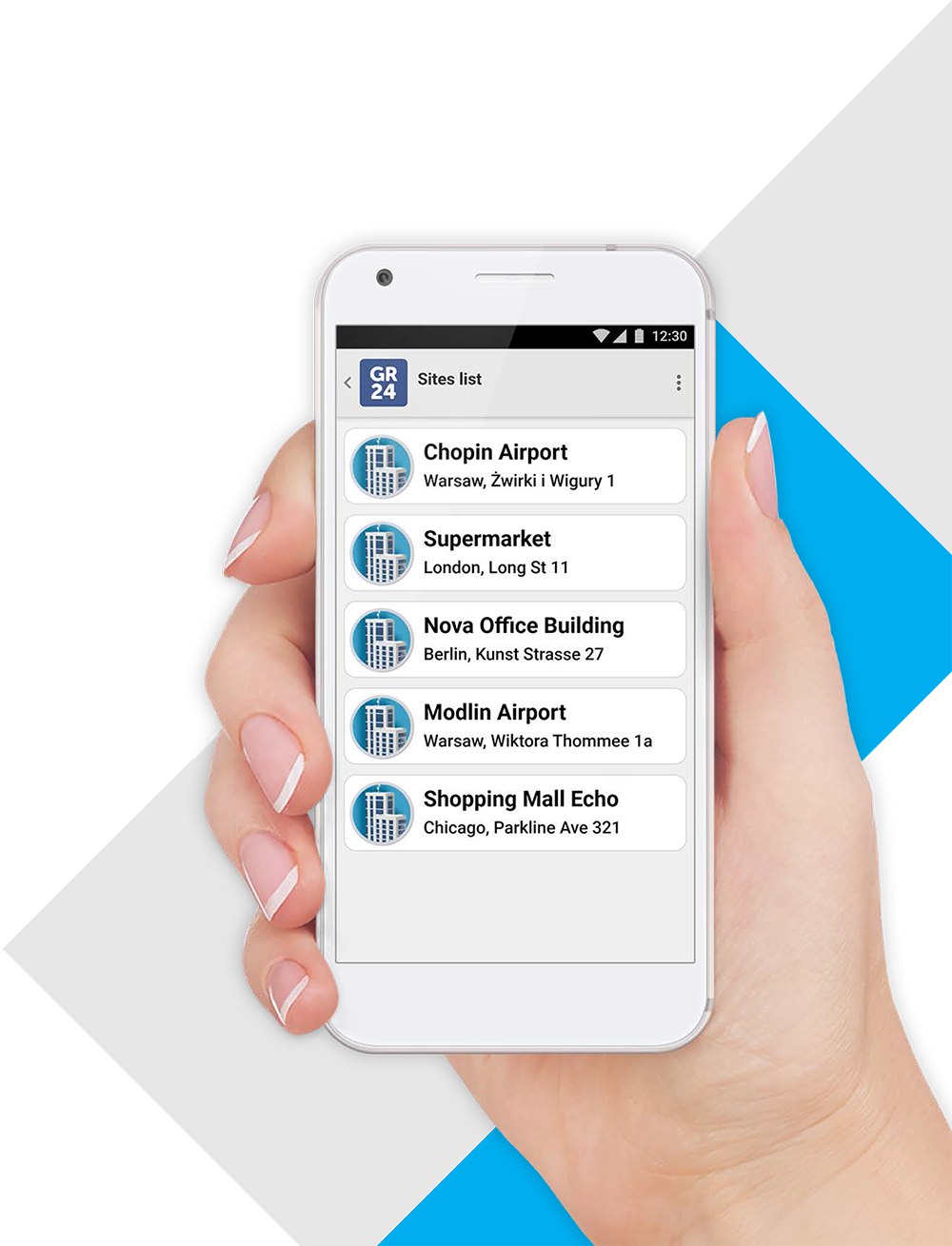
Selection of objects
If login completes successfully, a list of objects to which the user has rights will be displayed.
Objects can be added and deleted dynamically so that they will appear (and disappear) without having to log out of the application.

To-do list
After selecting the object, a list of tasks that should be performed on the given day will be displayed. At any time, the user can check what tasks have already been done.
Tasks can be of three types:
- confirmation is just a click on the smartphone
- confirmation requires NFC point reading (analogous to RFID points in the round devices)
- confirmation requires scanning the QR code.
Performing the task
After selecting a specific task, a message will be displayed asking you to confirm it.
When the task is successfully completed, the application will display an appropriate notification.

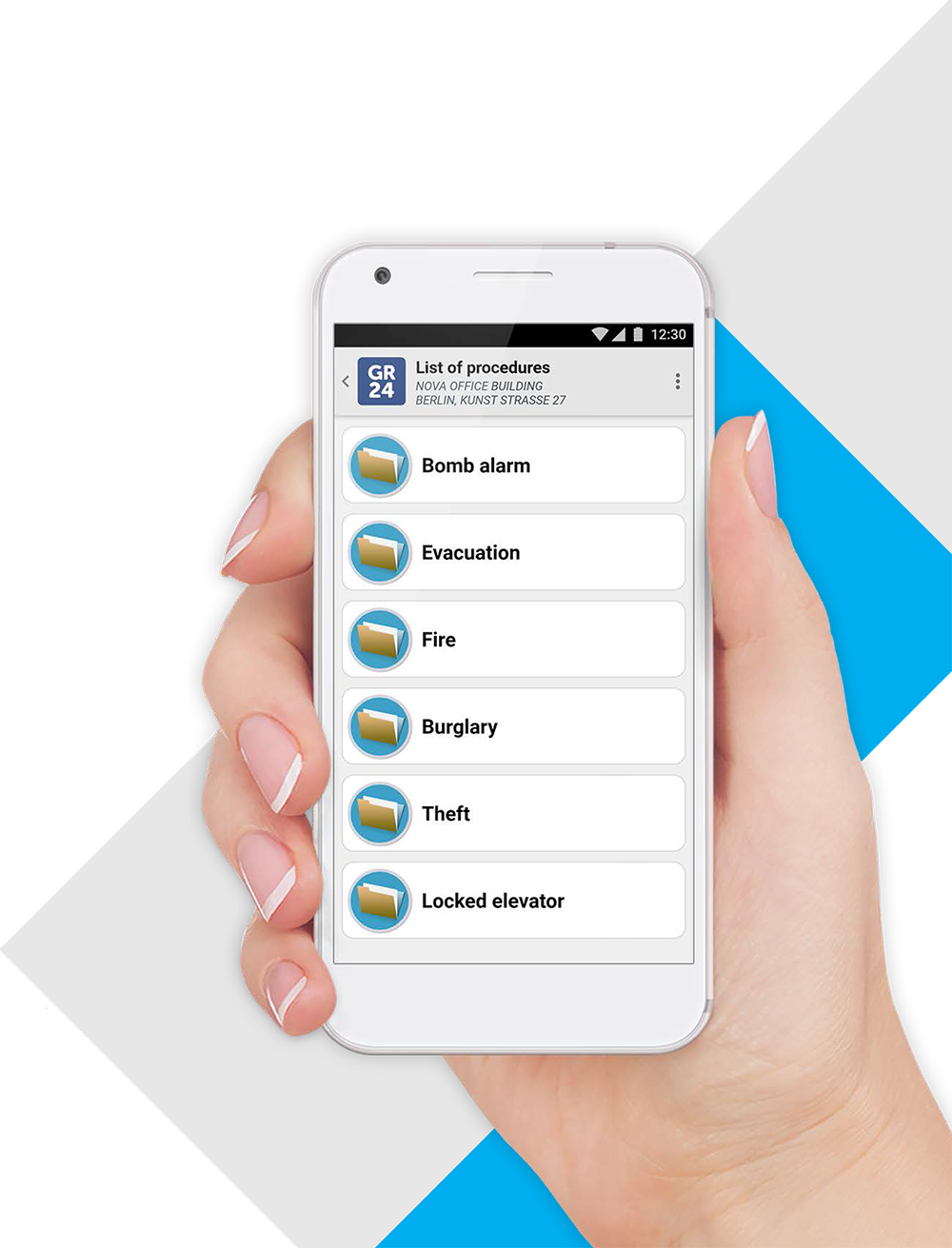
Access to procedures
It is extremely important that security personnel constantly have access to the procedures in force at the facility. All current procedures, along with their handling steps, are available in the mobile application. You do not even need to be connected to the Internet to check them.
NOTE: If the security officer proceeds to perform the procedure, he or she can report its occurrence, so an event will appear at the monitoring station. The steps of the procedure handled by the security guard become a description of the event.
The monitoring station uses a web application, where there are alarms of missing tasks, security incidents reported by security personnel and procedures carried out. The web application does not require installation. It is not necessary to use the functionality for monitoring stations, but it is a good element to provide security services.
Reporting activities
The to-do list applies to scheduled activities. If something unplanned happens – whether it’s a routine or an incident – a security officer reports it via a mobile application. Thanks to this in the object’s history there is an appropriate entry, which you do not need to report, because the client has access to reports.
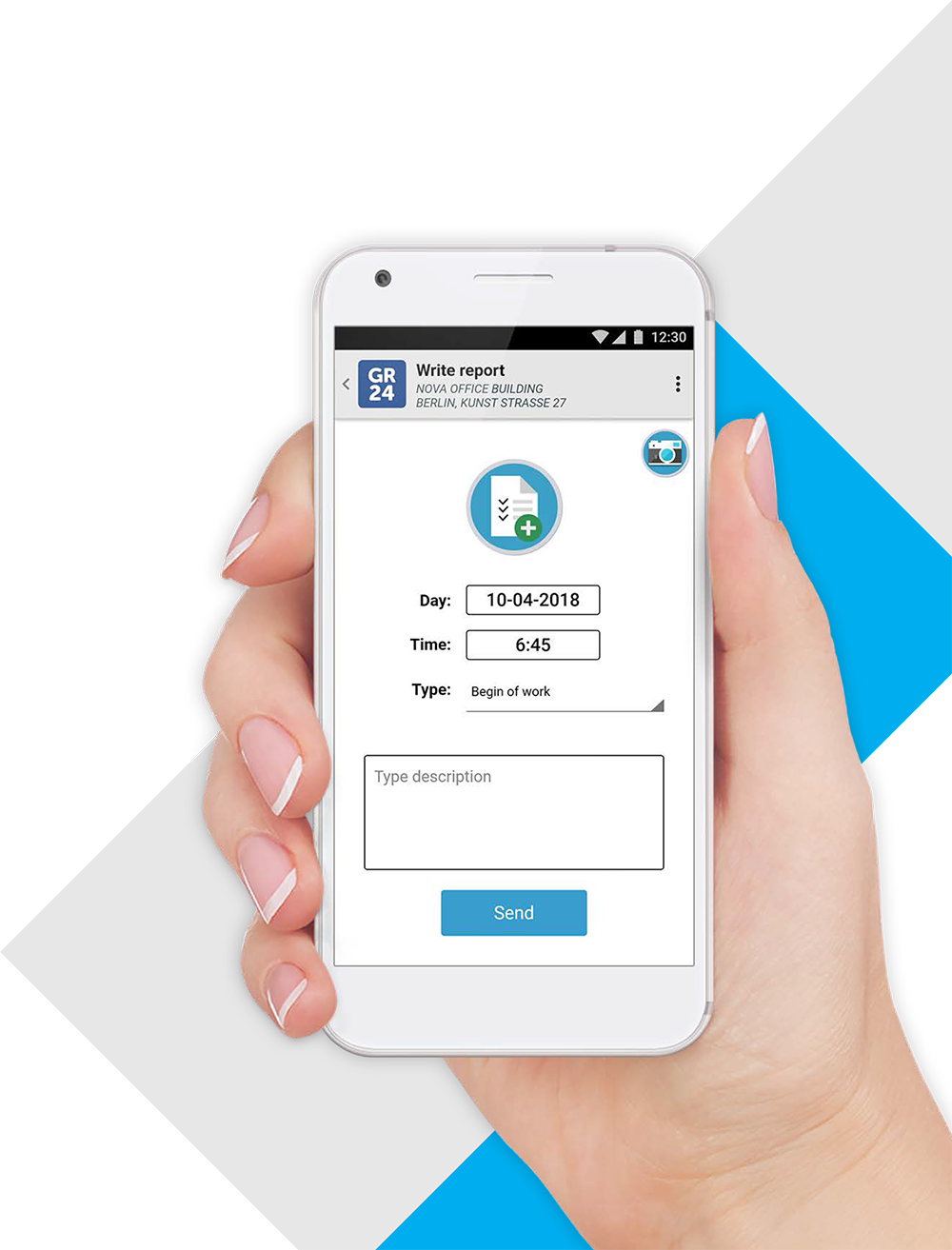
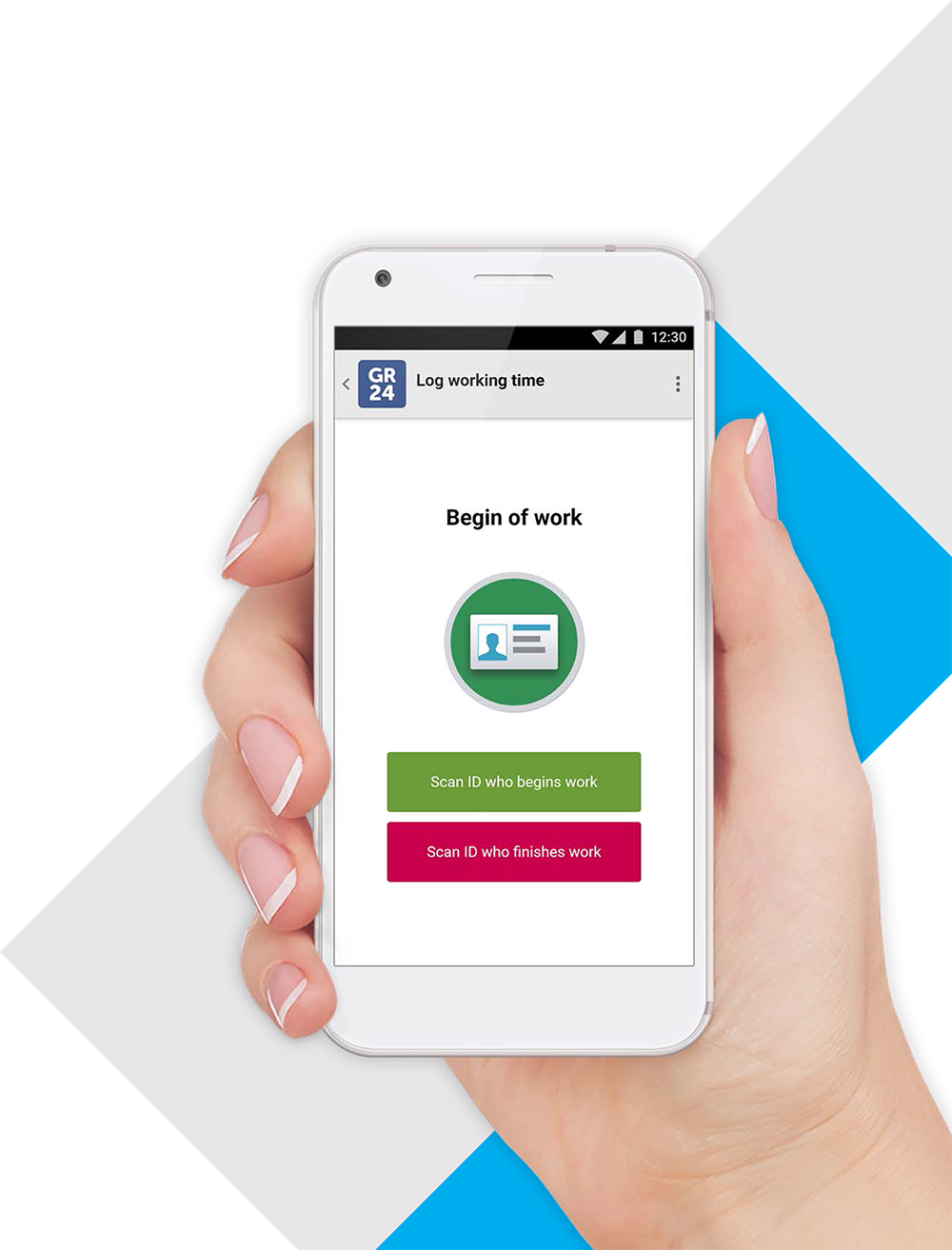
Control over working time
It is very important that the security company has control over the working time. The mobile application has the ability to confirm the beginning and end of the work of each security guard. This is done by scanning employee IDs printed on NFC cards in the same way as access control cards.
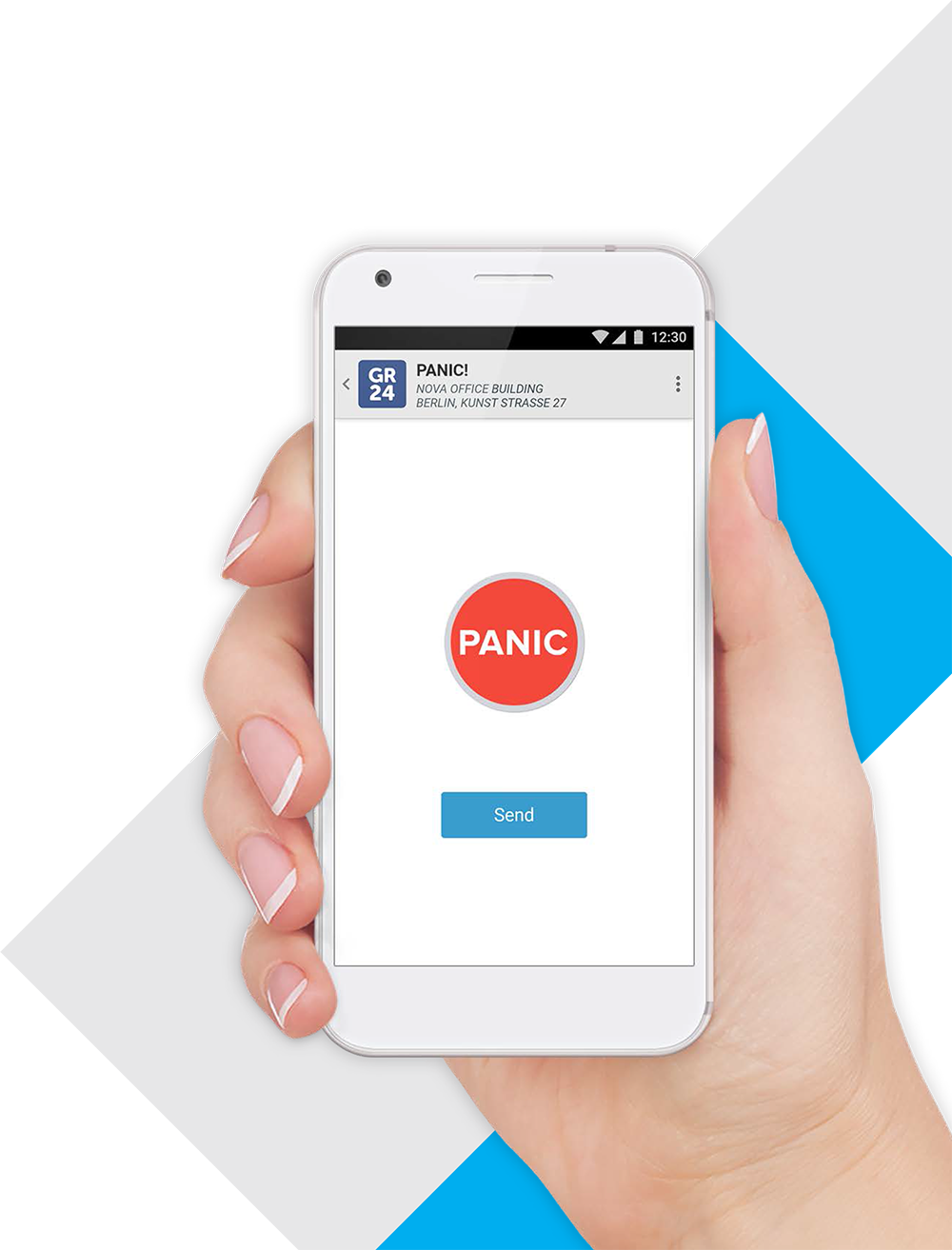
PANIC - alarm reporting
In crisis situations, at any time, the security guard can report an alarm via the app. The event is automatically visible at the monitoring station.
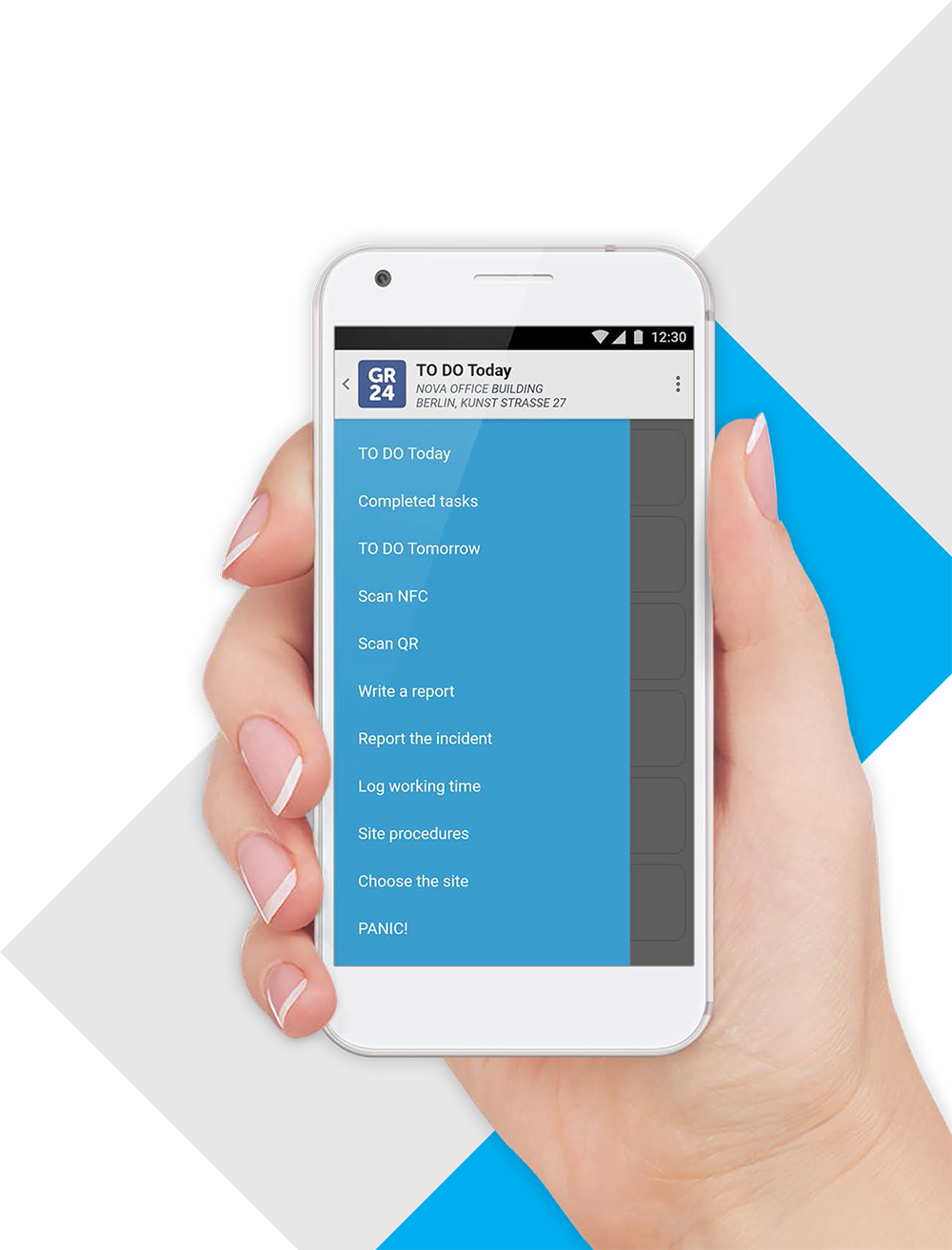
Navigating in the application
The intuitive interface of the application allows for easy and fast navigation. All basic tasks can be implemented from the main menu level.
